Note: This blogpost is also posted on the peppercrew website.
The Story
One of the great features you get when deploying a Windows operating system using my favorite deployment tool, the Microsoft Deployment Toolkit (MDT), is the ability to update the OS using either Windows Update or a local WSUS server. The latter is obviously preferred because it’s a lot quicker and you have better control over what updates you want to install. WSUS has a feature called Target groups, which you can utilize for managing update approvals for a group of computers. This way you’ll be able to approve or decline specific updates for Remote Desktop Session hosts or Exchange servers etc. While MDT let’s you specify a WSUS server to get updates from there’s no way to specify the target group you want to receive updates from. Let’s fix that, shall we?
How to create a variable
First you’ll have to create a new task sequence variable called TargetGroup. This can be done by altering the customsettings.ini. You can either open the file directly from your deployment share in the Control folder or right-click the deployment share in the DeploymentWorkbench console, choose properties and go to the Rules tab. All the way at the top you’ll find the Settings section. There you’ll find a property called properties. By adding TargetGroup as a value the variable will be created. You can create more by seperating them with a comma. The result should look like this:
[Settings] Priority=Default Properties=TargetGroup
Now that you have made the variable available you can give it the appropriate value. We’ll cover two methods of accomplishing this:
- Using CustomSettings.ini. Use this technique if you’re deployment share only requires one target group or if you have multiple section defined for machine deployments.
- Editing the Task Sequence. Use this technique if you need to have a different target group per task sequence.
Using customsetting.ini
You can set the value of the in the section of your choice. In this example we only have the Default section available so we’ll put it in there.
[Settings] Priority=Default Properties=TargetGroup [Default] TargetGroup=Terminal Servers
If you have multiple sections set up in your ini file, for instance Mac Address sections, you can set different values per section.
Editing Task Sequence
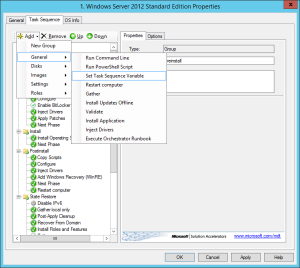
Open the properties of the task sequence and go to the Task Sequence tab. Click on Add – General – Set Task Sequence Variable.
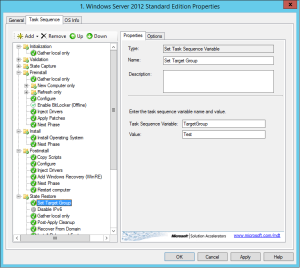
Enter TargetGroup in the Task Sequence Variable textbox and the name of your Target group in the Value textbox. You can also edit the name if you like. Click Apply when your done and voilá, you’re done:
Editing the MDT update script
Now that we have our brand new variable set up it’s time to let MDT know what to do with it. Open Windows Explorer and go to your deployment share’s Script folder. Open the ZTIWindowsUpdate.wsf file in your favorite editor (I like Notepad++) and look for the Configure Windows Update settings section. It’s usually around line 555. Add the following lines in the first IF statement:
If oEnvironment.Item("TargetGroup") <> "" then
oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroup", oEnvironment.Item("TargetGroup"), "REG_SZ"
oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroupEnabled", 00000001, "REG_DWORD"
End if
The end result should look like this:
'//----------------------------------------------------------------------------
'// Configure Windows Update settings
'//----------------------------------------------------------------------------
If oEnvironment.Item("WsusServer") <> "" then
' Configure the WSUS server in the registry. This needs to be a URL (e.g. http://myserver).
oLogging.CreateEntry "Configuring client to use WSUS server " & oEnvironment.Item("WsusServer"), LogTypeInfo
oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUServer", oEnvironment.Item("WsusServer"), "REG_SZ"
oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUStatusServer", oEnvironment.Item("WsusServer"), "REG_SZ"
If oEnvironment.Item("TargetGroup") <> "" then
oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroup", oEnvironment.Item("TargetGroup"), "REG_SZ"
oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroupEnabled", 00000001, "REG_DWORD"
End if
End if
Save the file and you’re done! In my next post I’ll get into creating a Windows Update custom wizard page so you can be more flexible with updates during deployments.
Later!


Hi Micah!
Thanks for this great post!
I worked for me.
But after reinstalling the WSUS server (remove roles en reinstall) The Target group is not working.
Do you have any suggestions?
Thanks! Regards
Have found the solution (facepalm).
Options –> Computers –> and select “use group policy or registry settings on computers”
Thanks!
You beat me to it! Glad to hear you found the post useful.
Is there a way of seeing what patches have been applied and approved to a Target group.
Thanks
It’s possible to script this but isn’t that what the WSUS console is for? I’m not sure what the added value is for having this information in your Deployment Wizard. I guess you could create a View Updates button and query the updates using vbscript or powershell (if you have powershell in your PE).
Thanks for the post. I had to tweak the additions to the script a bit to get it working. This is what I ended up with:
If oEnvironment.Item("WsusServer") <> "" then ' Configure the WSUS server in the registry. This needs to be a URL (e.g. http://myserver). oLogging.CreateEntry "Configuring client to use WSUS server " & oEnvironment.Item("WsusServer"), LogTypeInfo oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUServer", oEnvironment.Item("WsusServer"), "REG_SZ" oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUStatusServer", oEnvironment.Item("WsusServer"), "REG_SZ" End if If oEnvironment.Item("TargetGroup") <> "" then oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroup", oEnvironment.Item("TargetGroup"), "REG_SZ" oShell.RegWrite "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroupEnabled", 1, "REG_DWORD" End ifChanging the DWORD to just 1 instead of 00000001 makes sense. I’ve had no issues with my original value but if it works for you then thank you for sharing your solution.
PS. I edited your comment to improve readability and because the <> symbols were being left out by the html code.
Hi Micah
Actually all ending brackets combined with ” and some of the following characters are thrown away..
Regards
Thomas Ehler
Great information, thank you from a newcomer to the MDT world.
Thanks for telling us how to get the TargetGroup to the deployment. But I have the problem, the my WSUS server uses SSL port 8531. So I tried to import my own RootCA to the local computer store by a task sequence: cmd /c certutil -addstore ROOT “\\server\ShareName\Certfile.cer”
But this ends allways with an error:
Litetouch deployment failed, Return Code = -2147467259 0x80004005
I did not find the certificate in the local store.
When I remove the task from task seqeuence, it works well; without certificate…. 😦
Can you help?
There’s not much to go on with only that error code. Is there anything specific in the deployment log files? Here’s what I think happens:
MDT installs everything using the local administrator account so if you use a UNC path to a certificate file that is probably going to fail (local administrator account has no rights on remote shares). You can solve that by doing either of two things:
* Importing the certificate as a MDT application with source files and use “cmd /c certutil -addstore ROOT CertFile.cer” as install command.
* Edit your current task in the TS by specifying an account the command line should run under. Make sure the account has rights on the share where the certificate is located.
Good luck!
I’m a newbie in terms of scripting and using notepad++, but once you open the script with it do you simply paste the lines you referenced in your post?
Yes, as long as you paste them in the right section and add the custom variable to your ini file.
“MDT installs everything using the system account”
I don’t think it does. SCCM does, but MDT always uses the local admin account. Also, your code seems to be missing quotes and parenthesis probably due to the conversion to HTML on WordPress. Not sure if it’s something you can address.
You’re right. I meant local administrator. I’ve corrected the comment. As for the missing quotes and parenthesis: I’ve gone through great lengths to make sure the html doesn’t mess up the code and everything looks normal on my end. Maybe it’s a question of locale settings?! Is there a way you can show me a screenshot? Here’s what it looks like over here:

The part that is missing quotes and parenthesis is getting chopped off (possibly by WordPress?) in the screenshot you provided. I don’t see a way to post a screenshot of my own without logging in so I guess I’ll try to paste the raw text, but who knows how that will show up considering the issue. Here are the line endings that appear to be wrong:
URL (e.g. http://myserver).
oEnvironment.Item(“WsusServerogTypeInfo
Windows\WindowsUpdate\WUServer”, oEnvironment.Item(“WsusServerREG_SZ”
Windows\WindowsUpdate\WUStatusServer”, oEnvironment.Item(“WsusServerREG_SZ”
ft\Windows\WindowsUpdate\TargetGroup”, oEnvironment.Item(“TargetGroupREG_SZ”
ft\Windows\WindowsUpdate\TargetGroupEnabled”, 1, “REG_DWORD”
Word wrap is not my friend =/
I have done like above and the task is working, it install patches and reboot nd so on.
But he problem is that it install EVERYTHING. I just want to get security patches but i just dont understand how and where i shall config this.
Shall i create som Group on the wsus server? Where on the wsus server can i say that my server that i want to patch will only get security patches?
I still want to be able to patch for example clients with both updates and security so i dont want to change anything on the wsus server so it will be broken.
What you need to do is create a new Target group in WSUS and approve only security updates for that group. Then, when you deploy the server using the Targetgroup variable, only the security patches will be installed.
thanks, but how will i create this target Group in wsus server? 🙂
maybe i do it under the computer node, under this node i have today for example unassigned computer. My test server is inside this folder unassigned computer.
Is it just to right click and create Group and then i will be asked for what patches i want to be applied?
And this Group MUST have the TargetGroup, or?
and i dont want to add my computers manually into this Group, i want them to pop in to this Group automatically
“and i dont want to add my computers manually into this Group, i want them to pop in to this Group automatically”…
That’s exactly right. You can’t manually move the computers to the group. In WSUS there are two ways to assign computers to groups. Either via the console or via the client. This method is via the client. You need to create the group in the console and approve the updates for that specific WSUS group. Unassigned is where computers go if they have not been assigned a group. If you are using groups like explained above I would recommend you do NOT approve updates for unassigned computers. It will only cause you grief.
Also, in order for this to work you must change the setting on your WSUS server so it allows clients to assign their own group. Not sure which version of WSUS you use, but that hasn’t changed:
https://technet.microsoft.com/en-us/library/dd939829%28v=ws.10%29.aspx
we use this version: 6.3.9600.18228
Somehow my server has now been added into the Group in WSUS console, so that means that all things in MDT seems to work fine now. It create the correct variable and so on.
The last thing now i dont understand, how do i only add security patches to my newly Group inside wsus console? I can to anything with it. Just add more computers, search and refresh, sort of.
Please give me a guide how i now can say that servers in this Group will only have security patches installed.
I might find something now.
1. Rightclick security updates under Updates node
2. New update view
3. Click updates are approved for a specific Group…….
and then in the lower windows, precis specific Group and Point to your Group
4. Specify a new name.
Is that all? 🙂
A view can filter and display updates any way you want. What you are explaining would only show you updates that are already approved for a specific group. You wouldn’t want to filter by group if you haven’t yet approved them. Obviously they wouldn’t show up until you approve them. If you want to approve them you have two options. One option is create an update view that shows you whatever updates you want to see. For example, I could create a view that only shows me Windows Server 2012 R2 Security updates. Once you create the view then click the filter at the top of the window that says “Approval:” and pick the Unapproved option. That would show you all updates that have not been approved. You could then individually or multi-select updates and right-click–>Approve. That will open a window so you can pick which WSUS group you want to approve them for.
Personally I don’t manually approve most updates. I setup automatic approval rules for Critical, Definition, Security Updates, and Updates. I don’t auto approve things like update rollups, feature packs, and service packs. So for security updates you could go to Options–>”Automatic Approvals” and setup a New Automatic Approval Rule that approves all security updates specifically for a specified WSUS target group called Servers for example. As updates are released by Microsoft WSUS will automatically approve the ones you setup a rule for. That will cause the WSUS server to download them and release them to the clients. In your case it will make them available to MDT when the specified target group looks for updates for the “Servers” group.
Thanks. I will keep on trying this tomorrow at work.
I think we alrady have a approval rule that approve all security updates. If i have this automatic rule and i have right click on the node security update and point that to my newly created group, will that group then always have all security updates that i have approved in the security folder?
It is hard to explain in words what i am want this to do. Hope you understand what i am trying to achieve.
I created a new filter today and ticked my target Group and also only security updates and then start the scrip again. Unfortanly it still install everyting and not only security patches. The server is visable in the target Group i have been created, so this part seems to work fine.
When you say: “I started the script again” do you mean you’re using this script as a standalone solution? This script was made for use in MDT to install WSUS updates during deployment. If you’re using it as a standalone script you don’t have Task Sequence variables to work with and that will give you unexpected results. Please check in the registry if the correct Target group is set on the client, otherwise you’ll never have control over the update installation.
what i meant was that i started the script manually on my server i want to patch. This script is on the MDT server so i start it from a network share on the MDT server. Everything is working correct,my server will be patched but i get all patches and not only security patches that i have config in new update view, so i dont use it standalone. I have checked in registry and corerct values is set during script and my server is also being added inside my target Group. I have a task that is setting this variable up like the above instruction. So i Think i have come a lot further, but now i really dont understand why i still got all patches.
Lars, you have either implemented MichaH’s solution incorrectly or you have more updates approved for that target group than what you think you have. When you say “I created a new filter today” what do you mean by that? Is that a new update view?
yes, i meant a new update view. When you do that there is some options to make, for example target Group, what patches and so on
We to to identify where your problem is. Open up the Windows Update log under c:\Windows\WindowsUpdate.log. Search the log for “target group” (without the quotes). That will tell us what the Windows Update agent is actually doing. Does the agent show that it’s in the target group or is it null?
Great idea and it’s obvious that this works for most people, however I only seem to get “Dirty Environment Found” messages. I do not require the use of different TargetGroups per Task Sequence so the simple addition to Custom.ini and the WindowsUpdate script should suffice.
However I get the above error during the application installation task sequence and the report at the end reveals that the WindowsUpdate task has failed. Any idea what could be the cause?
Thank you
My Custom .ini contains:
Properties=DriversApplied,TargetGroup
[Default]
TargetGroup=Win 7
My script appears as follows:
‘//—————————————————————————-
‘// Configure Windows Update settings
‘//—————————————————————————-
If oEnvironment.Item(“WsusServer”) “” then
‘ Configure the WSUS server in the registry. This needs to be a URL (e.g. http://myserver).
oLogging.CreateEntry “Configuring client to use WSUS server ” & oEnvironment.Item(“WsusServer”), LogTypeInfo
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUServer”, oEnvironment.Item(“WsusServer”), “REG_SZ”
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUStatusServer”, oEnvironment.Item(“WsusServer”), “REG_SZ”
If oEnvironment.Item(“TargetGroup “” then
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroup”, oEnvironment.Item(“TargetGroupREG_SZ”
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroupEnabled”, 1, “REG_DWORD”
End if
End if
oLogging.CreateEntry “Configuring Windows Update settings (manual update, use server)”, LogTypeInfo
If oEnvironment.Item(“NoAutoUpdate_Previous”) = “” then
On Error Resume Next
iNoAutoUpdate = oShell.RegRead(“HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\NoAutoUpdate”)
If iNoAutoUpdate = “” then
iNoAutoUpdate = “”
End if
oLogging.CreateEntry “Archive NoAUtoUpdate State: Was [” & iNoAutoUpdate & “].”, LogTypeInfo
oEnvironment.Item(“NoAutoUpdate_Previous”) = iNoAutoUpdate
On Error Goto 0
End if
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\UseWUServer”, 1, “REG_DWORD”
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\NoAutoUpdate”, 1, “REG_DWORD”
‘ Restart the service to get the latest settings
oShell.Run “net stop wuauserv”, 0, true
oShell.Run “net start wuauserv”, 0, true
There’s a lot of characters missing in your code, but that’s probably because of html. Can you repost the script in a code block? That should take care of the missing chars. Are there any errors in the ZTIWindowsUpdate.log?
That sounds like the result of an unexpected reboot. I don’t see how it could be related off the top of my head. Seems like you may have a problem with something else. What is the last step that completes when you get the unexpected reboot? Is it actually working on Windows updates when it happens?
Hello! Thanks for your post.
I want to create two custom sections in MDT and pass the values to custom settings.ini
The lines that i’ve been created are:
[Settings]
Priority=Country, CProfile, ByLaptopType, ByDesktopType, ByVMType, Default
Properties=MyCustomProperty, NameByType, NameByLocation
[Country]
001=COLOMBIA
002=VENEZUELA
003=USA
004=ECUADOR
‘ // Países y su respectiva configuración
[VENEZUELA]
UserLocale=sv-se
UILanguage=sv-se
KeyboardLocale=041d:0000041d
TimeZoneName=Pacific Standard Time
NameByLocation=V
[COLOMBIA]
UserLocale=sv-se
UILanguage=sv-se
KeyboardLocale=041d:0000041d
TimeZoneName=Pacific Standard Time
NameByLocation=C
[USA]
UserLocale=sv-se
UILanguage=sv-se
KeyboardLocale=041d:0000041d
TimeZoneName=Pacific Standard Time
NameByLocation=U
[ECUADOR]
UserLocale=sv-se
UILanguage=sv-se
KeyboardLocale=041d:0000041d
TimeZoneName=Pacific Standard Time
NameByLocation=E
‘ // Establece la configuración se aplicará por perfil
[CProfile]
011=J-UP
012=USERS
013=POS
[J-UP]
Home_Page=http://www.UP.comv
[USERS]
Home_Page=http://www.USERS.com
[POS]
Home_Page=http://www.POS.com
Doing something similar will work with my MDT or the process with custom sections and subsections are different?
Thanks in advance.
Jason Corchuelo.
Hi Jason. The process seems fine. You have a lot of properties in your Priority setting that are not native to MDT. How are these being created and set? Are you using custom panes for that?
Please check this article. It works but only after you pay attention to the errors in the script formatting. I’m assuming the website is removing things.
Can you specify what get’s screwed up on your end? Because on my system all is looking well.
I’ve noticed it depends on the browser you’re using. In Chrome everything looks fine but in Edge the closing brackets are missing. Very annoying, indeed.
Should be better now. Thanks for the heads-up.
Awesome, I refer to this page each time I build MDT. Just to confirm this customisation works for MDT 8450 no problems.
I was just about to re-implement these changes after updating MDT and when I went to copy the code it doesn’t look right to me. The comparison operators are missing in the “If” statements. I tried Chrome, Firefox, and IE. They’re missing in every browser. Are you using a WordPress plugin for code snippets? You might want to try this one https://wordpress.org/plugins/code-snippets/. Haven’t used it myself, but it seems to be a pretty popular one. Guessing it would help with some of the inconsistencies we’re seeing.
Also, MicaH it appears that MDT does not clean up these registry settings and I don’t think sysprep is cleaning it either. Probably not a huge deal in most cases, but I just discovered this and thought I’d pass it along. You may already be aware.
I’m aware of it. If you want you could add it to the ZTICleanup script. In most cases the WSUS client will be set by GPO so the registry keys will be overwritten.
Actually it would have to be LTICleanup.wsf. There is no ZTICleanup script. Thoughts on my other comment regarding code snippets?
You’re right. Sorry, I’m at home watching TV so I couldn’t check the actual name of the script. Regarding the code snippets: I thought I had fixed that about a week ago. I’ll check again tomorrow at work.
It’s fixed now. Thanks for pointing it out to me.
I’ve added SSL support for WSUS.
You will need another deployment variable names “WsusSecure” which stores the URL to you secured WSUS like “https://yourWSUS:8531”
ZTIWindowsUpdate.wsf need to contain:
‘//—————————————————————————-
‘// Configure Windows Update settings
‘//—————————————————————————-
If oEnvironment.Item(“WsusServer”) “” then
‘ Configure the WSUS server in the registry. This needs to be an URL (e.g. http://myserver).
If oEnvironment.Item(“WsusSecure”) = “” then
oLogging.CreateEntry “Configuring client to use non-secure WSUS server ” & oEnvironment.Item(“WsusServer”), LogTypeInfo
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUServer”, oEnvironment.Item(“WsusServer”), “REG_SZ”
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUStatusServer”, oEnvironment.Item(“WsusServer”), “REG_SZ”
Else
oLogging.CreateEntry “Configuring client to use secure WSUS server ” & oEnvironment.Item(“WsusSecure”), LogTypeInfo
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUServer”, oEnvironment.Item(“WsusSecure”), “REG_SZ”
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\WUStatusServer”, oEnvironment.Item(“WsusSecure”), “REG_SZ”
oLogging.CreateEntry “Configuring client to use WSUS alternate download server ” & oEnvironment.Item(“WsusServer”), LogTypeInfo
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\UpdateServiceUrlAlternate”, oEnvironment.Item(“WsusServer”), “REG_SZ”
End if
If oEnvironment.Item(“TargetGroup”) “” then
oLogging.CreateEntry “Configuring client to use WSUS target group ” & oEnvironment.Item(“TargetGroup”), LogTypeInfo
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroup”, oEnvironment.Item(“TargetGroup”), “REG_SZ”
oShell.RegWrite “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\TargetGroupEnabled”, 1, “REG_DWORD”
End if
End if
@MicaH If you like you can use this to update your article.
Oh… And don’t forget to install your WSUS certificates before searchin for Updates.
Still works for MDT 8456